War Stories: RIP ADT [part 1]
Here lies ADT
They said they were number one
But a hacker got bored
Swung his digital sword
And the ADT system was done
Foreword
A quick obligatory CYA before we get to the good stuff (tech purists, scroll on past):
- This is not a comprehensive assessment of all systems, sensors, configurations, and solutions ADT has to offer. These were my honest results when testing a single system, YMMV. It is possible that unknown factors invalidated my tests or otherwise contributed to the results I observed.
- I did not perform any illicit reverse engineering of ADT or Qolsys technologies, software, hardware, or signaling protocols in the course of this exercise.
- I did not perform any illicit wireless signal jamming or similar activities which would in any way violate regulations such as those set forth by the FCC and other authoritative bodies.
- No novel vulnerabilities or exploits were discovered or developed during this exercise. Thus, as there is nothing to report to the vendor, no responsible disclosure procedure was necessary.
- Some of these approaches may be applicable to other systems, but that is beyond the scope of this write-up.
- I do not have any affiliations with any alarm system providers or component manufacturers, nor do I attempt to make any endorsements of the same.
- My opinions are my own - you should do your own due diligence and draw your own conclusions.
- None of this is particularly groundbreaking.
- All testing activity was performed with the explicit authorization of the owner.
- This is for educational purposes only. If you use this information to break into someone's house, may God have mercy on you, because in all likelihood, the homeowner will not.
Introduction
I have always been interested in physical security, and although I have a mini-arsenal of relevant gadgets and have had the privilege of participating in a handful of physical intrusion operations, I have never had the opportunity to sit down and really spend some time exploring all the angles on a proper alarm system. What follows is the result of my curiosity and boredom. We will first go over the things I learned about this particular system, then wrap up with a step-by-step attack path, all the while putting ourselves in the shoes of a real-world threat actor. ADT acknowledges in no uncertain terms within their contract language that these systems can be hacked and furthermore that their effectiveness can be reduced by a person with criminal intent. Good thing thwarting criminals is not the core function of an alarm system, right?

This seems to be a pretty stark contrast to the way ADT markets themselves. As of this date, their website claims they are the leading provider in the US for these kinds of systems. If that is the case, the bar must be pretty low.

Reading through the rest of the contract terms is pretty enlightening, but I will leave that as an exercise for the reader - let's move on and dive into the fun stuff!
Alarm Panel
This ADT system uses a main control panel from Qolsys called the IQ Panel 2 which can communicate wirelessly with a variety of sensor types via a variety of protocols. This was sold by an ADT authorized dealer less than two years ago (in late 2021). While there are newer models of the IQ Panel available now, it appears that common ADT contract durations are 36-60 months, so this equipment is still relatively current.

Sensor Types
First, let's talk about the types of sensors in use. In our case, we are only working with door/window sensors and motion sensors, all of which are also Qolsys devices. There are a variety of other kinds of sensors which can be used with this ADT system which are outside the scope of this writeup - among these are CO sensors, flood sensors, cameras / imaging sensors, and glass-break sensors. CO and flood sensors aren't really relevant for the purposes of our assessment. As for cameras, if they communicate wirelessly using similar frequencies/protocols, we may be able to tamper with them the same way other sensors can be tampered with (more on that later). Regarding glass-break sensors, it sounds cool, but I expect these would be far less commonly encountered in a real-world implementation for a couple of reasons. The first reason is cost. In my house, I have a good number of windows, and as far as individual panes of glass go, the count is around 25. Assuming each pane needs its own sensor, 25 panes of glass at a cost of $50 per sensor would set you back a hefty $1,250 on top of the cost of the rest of your system. Keep in mind that a motion sensor can go for about $30, which leads us to the second reason I expect these would be rather uncommon - why would a homeowner put a glass-break sensor on every pane of glass in the room when one or two motion sensors can net similar coverage?
Door/Window Sensor Bypass - Old School
This article would not be complete without talking about the old tricks we've all seen in the movies. Of course, I would never let you down like that - we definitely need to validate how authentic these methods actually are! The key mechanism in these sensors is simple magnetism, so theoretically you could prevent a sensor from tripping by sliding a thin magnet into the door jamb between the sensor and the magnet before opening it. In practice, it appears that you need to select your magnet carefully. If you were hoping to grab a thin magnet from the fridge and slide it in like a credit card, you will be disappointed. It also seems that if the magnet is too strong, the technique will fail. However, with some trial-and-error, I found the "Goldilocks" zone and was able to successfully open doors without the sensor tripping the alarm. Speaking practically though, most doors/jambs/frames do not offer enough space to slide anything through, so you would need to whittle away a significant amount of material get your magnet through. Not exactly what I would call "stealthy", and if this is for a client engagement, not exactly what I would call "job security". But keep in mind that criminals do not care about permanent damage one bit, and with a bit of time and a cordless power tool, this is definitely feasible.

Motion Sensor Bypass - Old School
This is one of my favorite techniques, and soon you will see why. Many motion sensors use sonic waves to detect motion in a given area. In that case, you could drape a fabric over top of yourself to absorb the sound waves and move through the room slowly without detection. Just pretend it's Halloween and you're going as a spooky ghost! Ahhh! Other motion sensors, such as the Qolsys model in question, use infrared to detect motion in a given area. In this case, you could probably get away with holding up just about anything between yourself and the sensor as long as the material temperature is close enough to the ambient temperature in the room (I have seen teams successfully use Mylar in the past). In my case, this was successful and I was able to move across the room without tripping the alarm. The moment I lowered my "shield", however, it was game over! This is a somewhat workable solution, but as we will see, there are better methods available for bypassing these motion sensors, especially for a threat actor who is short on time and wants to avoid looking conspicuous the other 364 days of the year.

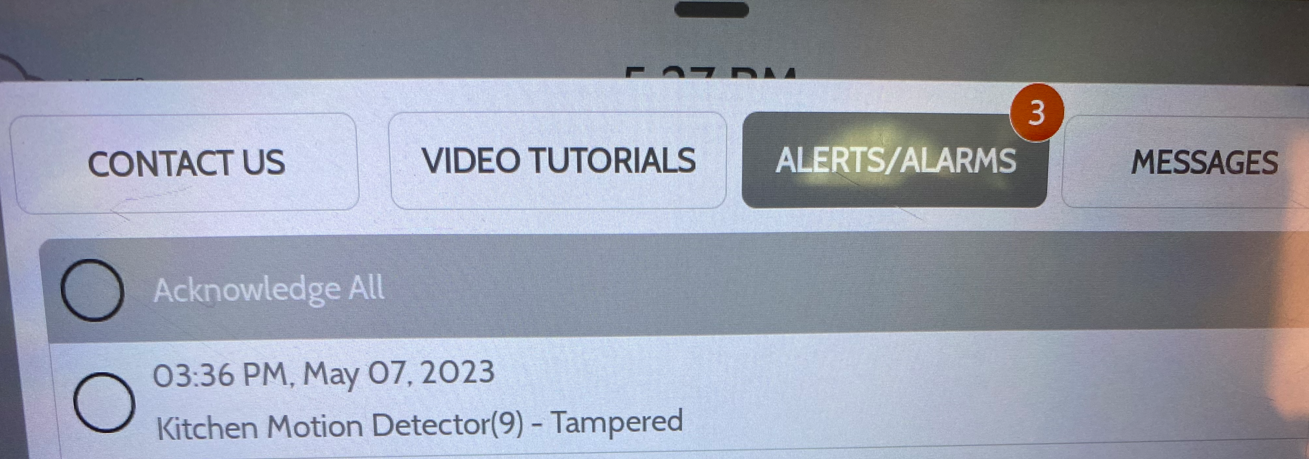
Tamper Protection
A quick note about "tamper" events - these are triggered anytime a chassis intrusion switch is tripped. These sensors are present in the door/window sensors, in the motion sensors, in the panel itself, and probably in other types of sensors as well. Unless you want to get caught, you will have to properly contend with these tamper protection mechanisms, or avoid opening device cases altogether. They can trigger email and/or push notifications to the system owner, and will activate the alarm if it is armed.
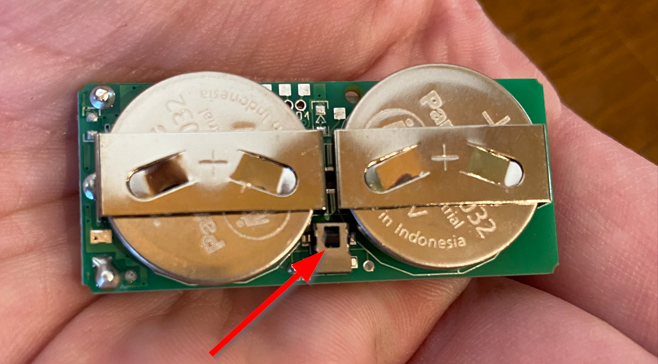
The chassis intrusion detection mechanism is essentially a small switch mounted to the PCB designed to trip when released, which occurs anytime the device chassis is opened. The switches on the door/window and motion sensors are pretty straightforward.

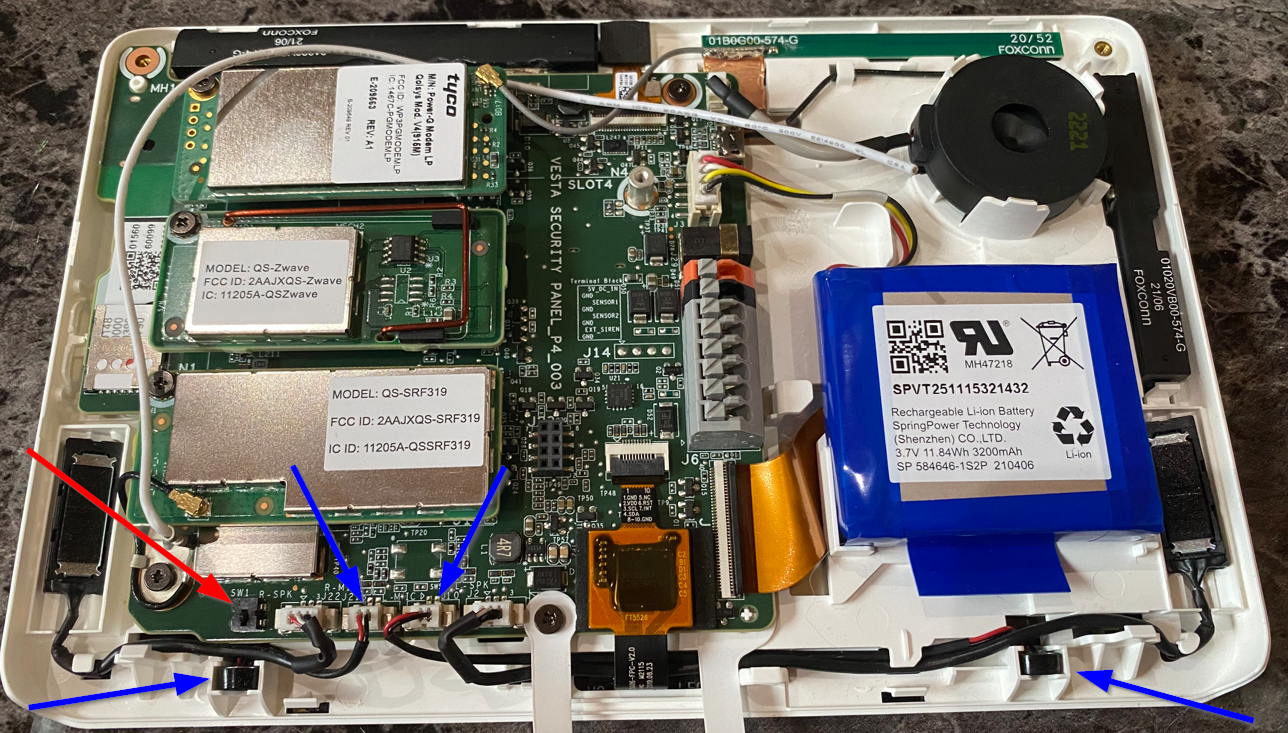
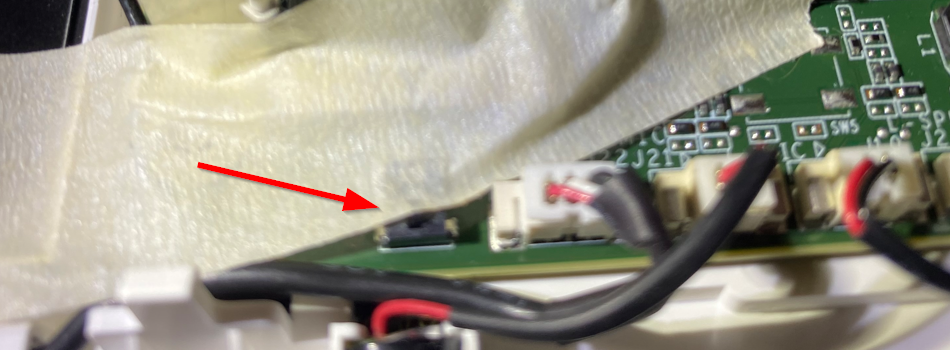
The intrusion detection mechanism on the panel itself threw me a bit at first. The components indicated in blue were what I initially assumed would trigger a tamper event, as each is mounted at the bottom of the panel behind a pair of buttons which must be depressed in order to "open" the panel by removing it from the wall mount. However, after some trial and error, I was able to confirm the panel switch is more or less identical to those on the sensors. Once this switch is taped down, you can close and re-open the panel without triggering a tamper event. You can even unplug the components in blue from the PCB and this still will not trigger a tamper event. Your guess is as good as mine regarding what those components are actually for.
Wireless Signals
The panel in question is able to communicate with a variety of devices and sensors via a number of wireless protocols. Among these are Bluetooth, Z-Wave, ZigBee, Power-G, and SRF. In our case, both the door/window sensors and motion sensors use SRF, so the others will be outside the scope of this writeup. Generally speaking, jamming a given wireless sensor can be done using a SDR broadcasting on the right frequency with adequate power. Since the frequency information is public, once you know what kind of hardware you are up against jamming is a fairly straightforward process. There are usually anti-jam mechanisms to trigger events similar to the tamper events we covered previously, but as other researchers have established, as long as the jam is temporary enough, you can avoid triggering the anti-jam mechanism. You should have more than enough time to get past a door/window sensor and cover up any motion sensors in the room before you need to stop jamming.

In our case, the Qolsys IQ SRF sensors are using the 319.5Mhz frequency. You could probably jam it just fine using something like the YARD Stick One SDR which goes for about $100. Qolsys documentation states that communication on this frequency by their devices is both authenticated and encrypted ("S-LINE" protocol), but you could get started analyzing it using something like this SDR for a mere $20. That is a pretty low barrier to entry, but I suppose it's better than alarm systems using 433Mhz sensors which can be jammed using a garage door opener.
Full Attack Path
- Jam the wireless sensors, quickly enter and close the door, cover the motion sensors with a piece of cloth or similar, then stop jamming before you trip an anti-jam tamper event.
- Do whatever you want and leave. Just kidding! That is what a criminal would do, but we are professionals, thus we cannot stop until someone on the team starts asking whether we should invoke "the slaughter rule".
- Tape the panel's built-in camera if you like. The panel can be configured to snap a photo when various events are triggered such as deactivation events, alarm activations, sensor events, and more. This shouldn't be strictly necessary, but why risk it?
- Open the panel without tripping the chassis intrusion detection mechanism. You could cut around the drywall and go in from the back, or you could cut around the edges of the wall mount carefully leaving the bottom-right corner intact to keep the switch depressed. If you have time, you could cut a small section out of the bottom-right edge and use some fine tooling to squeeze some tape between the switch and the part of the wall mount which keeps the switch depressed. The switch spring is very weak, a piece of masking tape will do the trick. Below you can see both the tab on the wall mount which keeps the panel intrusion switch depressed as well as the right-hand button you must press upward on from the bottom edge in order to "open" the panel (there is an identical one on the left-hand side). This is probably the hardest part.

- Disconnect the siren speaker from the alarm panel PCB. This will not trigger a tamper event or activate the alarm when armed. The siren isn't that bad anyways (some commercial systems I have experienced are truly painful), but just like the panel camera, why take the chance? Don't worry about the other two speakers on each side of the panel, they are used for general system audio output and are not used for the siren.
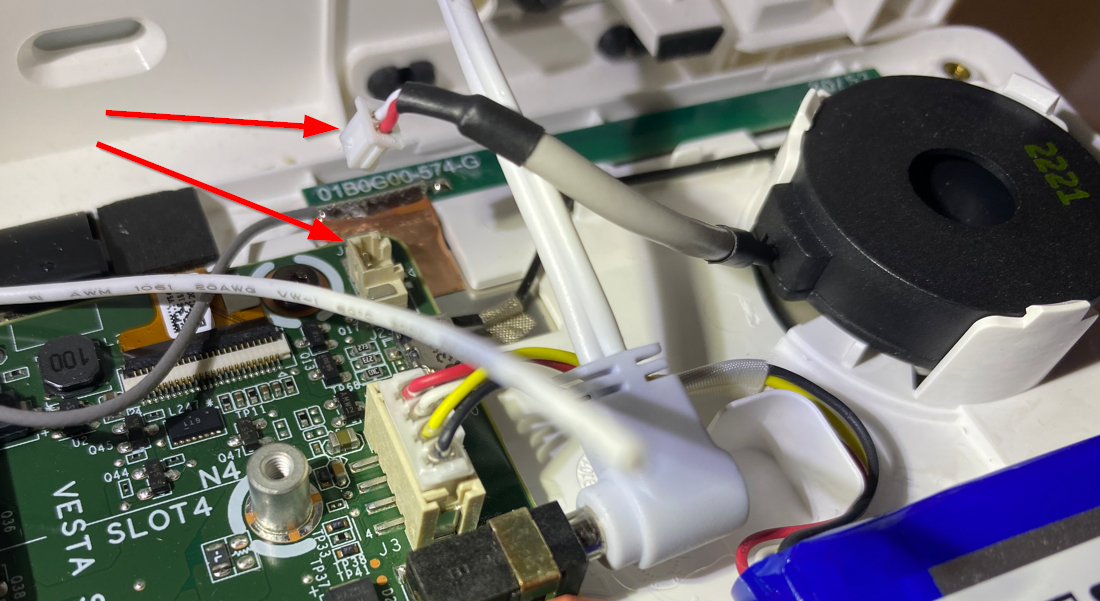
- Disconnect the internet edge device power source to effectively disable Wi-Fi and then remove the SIM card from the slot on the PCB so the system cannot phone home via either channel. Removing the SIM will not trigger a tamper event or activate the alarm when armed. There does not appear to be any emergency cell capabilities, alternate/embedded SIM, or other tertiary WAN mechanism based on my testing.

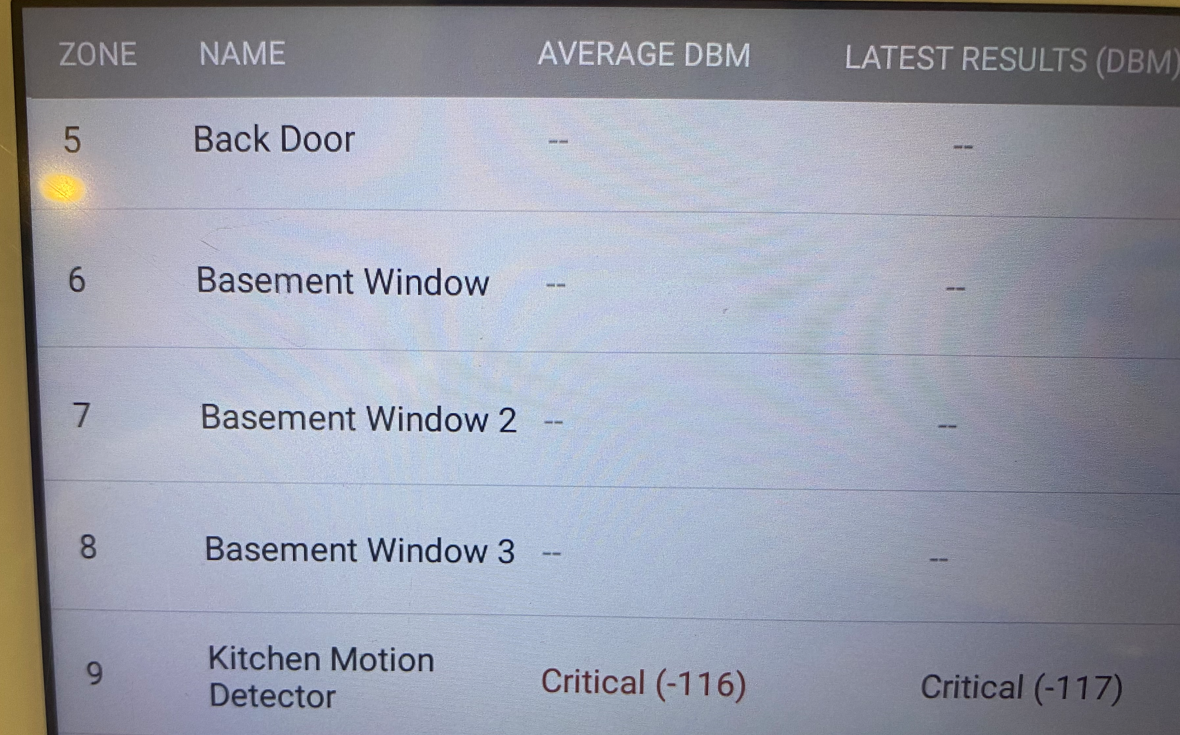
- Just for fun, you could go ahead and unplug the antenna for the SRF card. This effectively takes all sensors offline, but that is not really needed as you could just rely on jamming other sensors you want to bypass. In my test, the only sensor which was still online had terrible signal even though it was basically right next to the panel. In any case, this action did not activate the alarm when armed.

- The only thing left to do at this point is disconnect the AC power and the backup battery. Both of these actions will generate an event, but neither will activate the alarm when armed.
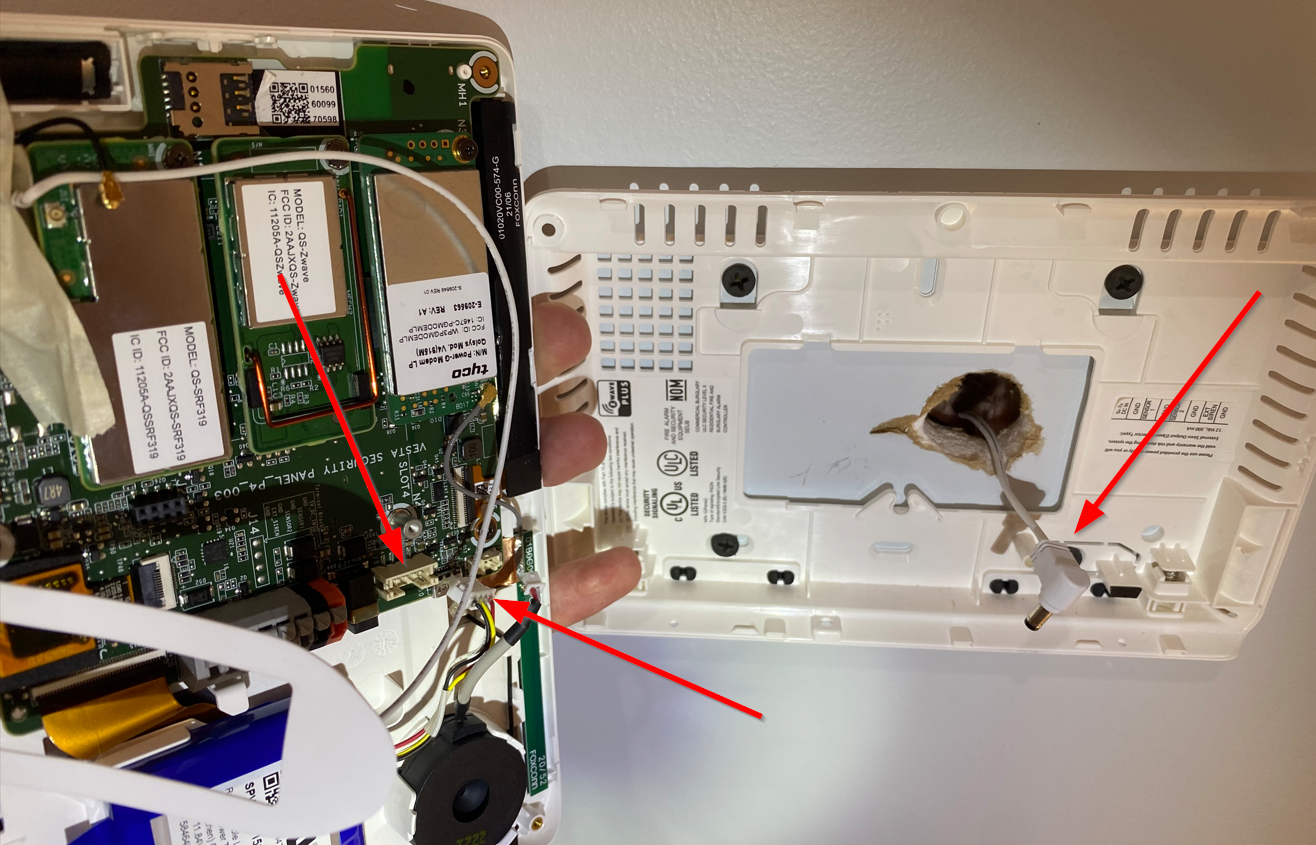
- At this point, I can hear my team yelling "overkill" so we will wrap it here. You can go ahead and take the alarm panel with you as a souvenir if you'd like.
Shouldn't ADT see that the panel went completely offline (primary and backup WAN, primary and backup power) when its last known alarm state was armed? Well if they did, it appears they did not act on it. In my case, I simply reconnected everything and let the panel boot back up, at which point the alarm was no longer armed.
Takeaways
- Do you want to feel secure, or do you want to be secure?
- Alarm systems are not silver-bullet solutions. Neither are locks or RFID access systems. Defense in depth. Dogs and sentries go a long way.
- Threat model your facilities. Take time to think through the angles, what you want to protect, and what a proportional solution would look like.
- Hire a consulting firm with teams which can perform physical intrusion testing.
- Do your due diligence, be innocent as a dove but wise as a serpent, and whatever you do, do not let the bad guys win.
Afterword
What about commercial systems? What about systems from other vendors/manufacturers or those using other wireless signaling protocols/frequencies? What about wired systems which do not rely on wireless sensors at all? What if I want to learn more about in-depth reversing of system signaling and logic? I recommend you take a look at some of these resources.
Last known photo of ADT is shown below.
Stay tuned for Part 2 in the RIP ADT series!
